Of the 16 human capital management (HCM) providers evaluated by Nucleus Research in its 2021 HCM Technology Value Matrix, two UKG solutions — UKG Pro™ and UKG Ready™ — have been named leaders. The designations are based on Nucleus’ assessment of relative usability and functionality of the solutions as well as the value customers have gained from each product’s capabilities. […]
Read more ›
7 Strategies for Growth
We are in the midst of the biggest single-year economic expansion since the 1960s. That’s the consensus from the International Monetary Fund, various U.S. government agencies, the Federal Reserve and most leading economists. The Conference Board predicts 6% U.S. GDP growth for 2021 after a 3.5% decline in 2020, and the Bureau of Labor Statistics confirms that, in the first […]
Read more ›
Technology Skill Development: The Strategy For Building Better Teams
Are you a leader at a rapidly growing or large company committed to embracing new technologies as they emerge? Are you part of a team that wants to be at the forefront of innovation and disruption? Are you looking to meet and adapt to customer demands faster, and with more agility, so you can be the first to market? Is […]
Read more ›
Handbook: Leading Remote Teams
The tech industry is reliant on the ability to pivot fast and evolve in an ever-changing landscape. The COVID-19 pandemic challenged that adaptability like never before. Every single business entity had to quickly stabilize, revise and rebuild to survive in a totally new reality. For a massive number of organizations, that meant shifting to remote work on a scale and […]
Read more ›
Perspectives in Engineering: 3 Ways to Help Your Team Thrive (In and Out of Codebase)
With help from top engineering leaders from across the world, this guide unpacks how to create the needed environment to help your team thrive in and out of the codebase. The insights are derived from peers who understand what it takes to create a high-performing engineering organization. By following the three main parts found in this guide, you’ll unlock new […]
Read more ›
2020 Vulnerability Intelligence Report
Security, IT, and other teams tasked with vulnerability management and risk reduction frequently operate in high-urgency, high-stakes environments that require them to quickly separate signal from noise. When a new potential threat emerges, information security professionals often find themselves needing to translate vague descriptions and untested research artifacts into actionable intelligence for their own particular risk models. Rapid7’s inaugural Vulnerability […]
Read more ›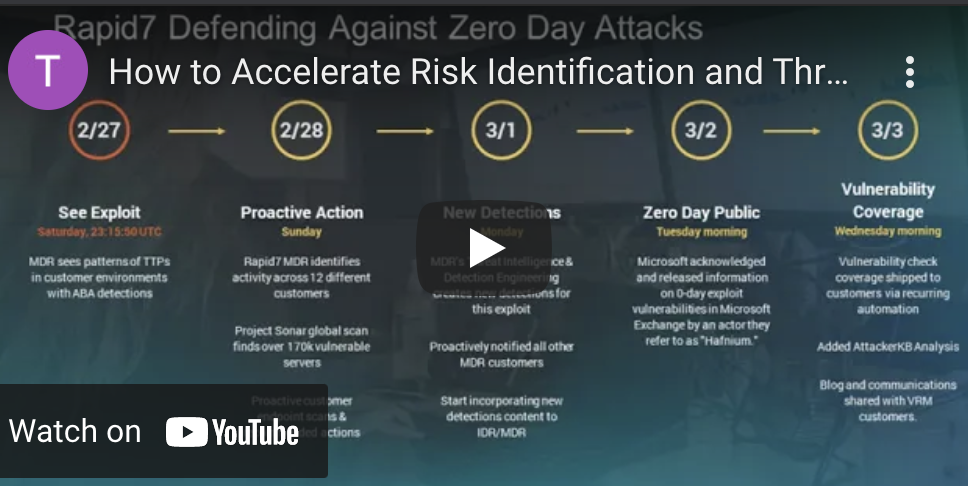
How to Accelerate Risk Identification and Threat Remediation
Discover how security teams battle the complexities of the industry with the Rapid7 InsightPlatform. The InsightPlatform is a holistic, cloud-based platform that can help accelerate threat detection and remediation with expansive visibility and risk coverage to minimize the attack surface. Watch this 10 minute talk to learn how the InsightPlatform leverages analytics, context and automation to detect and extinguish threats.
Read more ›
The Rise of Cloud-Based Security Analytics and Operations Technologies
How can CISOs address these issues and develop effective security analytics and operations processes? In order to get more insight into these trends, ESG surveyed 372 IT and cybersecurity professionals at organizations in North America (U.S. and Canada) responsible for evaluating, purchasing, and managing threat detection/response products, processes, and services. This eBook will cover how external changes and internal inefficiencies […]
Read more ›


