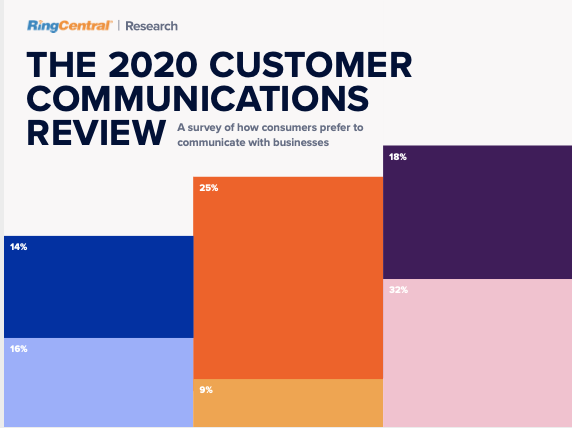
Do customers want you to email them or text them to confirm an appointment? How long is “too long” to wait on hold? Check out this survey of consumers’ preferences when it comes to communicating with businesses—and how you can reach out to your customers and prospects in a way that’s actually effective.
Read more ›
Migrating From a Premises-Based PBX to the Cloud: The Tide Has Turned
This webinar will cover questions that organizations should be thinking about: • What are the key benefits and drivers for moving to UCaaS?• What are the architectural options?• How should organizations migrate to the new service?• Why is NOW the time to migrate to UCaaS? You’ll hear from a leading industry analyst, as well as a customer that recently migrated […]
Read more ›
RingCentral Video Security
With the launch of the RingCentral Video platform to unify collaboration across a modern business environment, ensuring secure and private communications is a top-of-mind concern for business users and IT professionals alike. RingCentral Video is a modern online meetings experience powered by the market- leading RingCentral unified communications platform. It combines high-quality video, audio, screen sharing, and team messaging into […]
Read more ›
The Power of Connection – Why You Should Integrate Your Business Apps With UCaaS
Integrations today and tomorrow The modern enterprise relies on an array of different tools to boost productivity, automate workflows, provide customer relationship management and support, and manage communications both internally and externally. A Harmon.ie survey of information workers reports that, on average, 74% of employees have at least five apps open at one time and 16% use more than 15 […]
Read more ›
Advanced Protection for Web Applications and APIs on AWS
Tackle your web security challenges Companies of all shapes and sizes have embraced cloud-based web applications for mission critical workloads. But with each new application comes new challenges and risks associated with an expanding attack surface. More entry points. More security threats. This eBook explains how the evolving threat landscape impacts web applications and APIs and provides a checklist for […]
Read more ›
Why it Has Never Been More Important to Be a Qualified Cybersecurity Professional
Qualified Cybersecurity Pros Are More Important than Ever The business need for talented people represents a great opportunity for cybersecurity professionals like you. But future security leaders require a broad set of skills that job experience alone does not arm you with. This white paper from (ISC)2 examines the benefits and risks associated with increasing digitalization and how you can […]
Read more ›
Making Zero Trust Real
Establishing zero trust and least privileged access is key to securing privileged accounts. One Identity provides a holistic approach to implementing privileged access management (PAM) with these two proven methods. The Zero Trust model involves eliminating shared admin passwords and so that every administrative action is authenticated uniquely, dynamically and specifically. The Least Privilege approach involves delegating to give each […]
Read more ›
Zero Trust and Privileged Security for Hybrid AD
Learn How Zero Trust and Least Privilege Can Secure Access to Your Critical Resources. With the majority of large corporations using Active Directory (AD) and Azure AD to control user permissions and access, it is one of first places attackers look for weakness. And now that privileged access management (PAM) is a growing aspect of AD, it is becoming a […]
Read more ›