For years, Gartner has been ranking hyperautomation as one of the top strategic technology trends. For a perspective on how technology leaders can extend the concept of hyperautomation to visual media the right way, download our whitepaper Building Visual-Media Experiences at Scale with Hyperautomation
Read more ›
Technical Interview & Assessment Buyer’s Guide: Choosing a Vendor & Writing Your RFP
This guide will take you through everything you need to know to choose a technical interview & assessment vendor, including: • Defining your current technical hiring needs• Mapping key recruiting metrics to vendor requirements• Identifying common red flags in the live sales demo Your guide also provides a free, fully customizable RFP template that makes it easy to evaluate & […]
Read more ›
The Expert’s Guide To Increasing Diversity on Engineering Teams
Fact: Companies that are racially and ethnically diverse outperform industry norms by 35%. This guide brings together proven strategies from leaders in engineering and talent acquisition at leading companies for increasing diversity on your engineering team. These include: • Avoiding bias in technical questions• Conducting structured interviews• Leveraging expertise from IO Psychologists• And more
Read more ›
Merrick Protects Digital Assets from Ransomware
VMware Cloud DR named Outperformer in GigaOm DRaaS Radar Report Download the report to understand how VMware Cloud DR compares to other DRaaS solutions in the market. VMware Cloud DR offers on-demand DR, delivered as an easy to use SaaS solution, with cloud economics. “VMware Cloud DR utilizes VMware Cloud on AWS for the recovery environment, uniquely allowing integrated management […]
Read more ›
Addressing the Top 5 Challenges for Deploying Comprehensive DR Solution
Data and applications are critical for modern organizations to achieve their goals, which is why IT leaders commit significant resources to keeping them highly available, including preparing for a full site failure by creating a disaster recovery (DR) plan. Setting up a comprehensive traditional DR solution is difficult and expensive, and as applications evolve and data grows, organizations run into […]
Read more ›
How 3 Leading Companies Found Peace of Mind With Disaster Recovery
Many traditional DR solutions are unreliable, complex and expensive, requiring significant and time-consuming manual effort, and may not scale or provide the required levels of protection that organizations need. In fact, 69 percent of IT decision-makers lack confidence that they could reliably recover all business-critical data in the event of a cyber-attack[1]. As a result, customers including 888 Holdings, West […]
Read more ›
The VMware Guide to Disaster Recovery Readiness
When it comes to data, planning for the unexpected is of paramount importance—especially today. But long-term problems shouldn’t be solved with short-term solutions. Download this ebook for insights into building a DR plan, making an informed choice about the DR solutions available, and modernizing existing DR to optimize operational costs and accelerate recovery.
Read more ›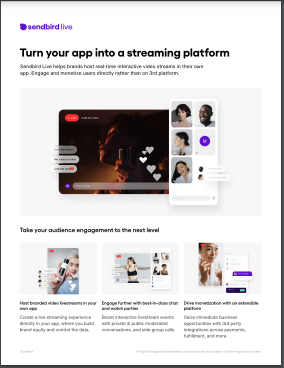
How to Turn Your App Into a Live Streaming Platform
Online live streaming is the single most engaging channel for worldwide audiences. Live streaming helps people create a deeper connection with your brand. Authentic, always on, and available on any connected device, live streaming produces the emotional connection brands need to drive loyalty. Why? 70% of emotionally engaged consumers spend up to two times or more on brands they are […]
Read more ›


