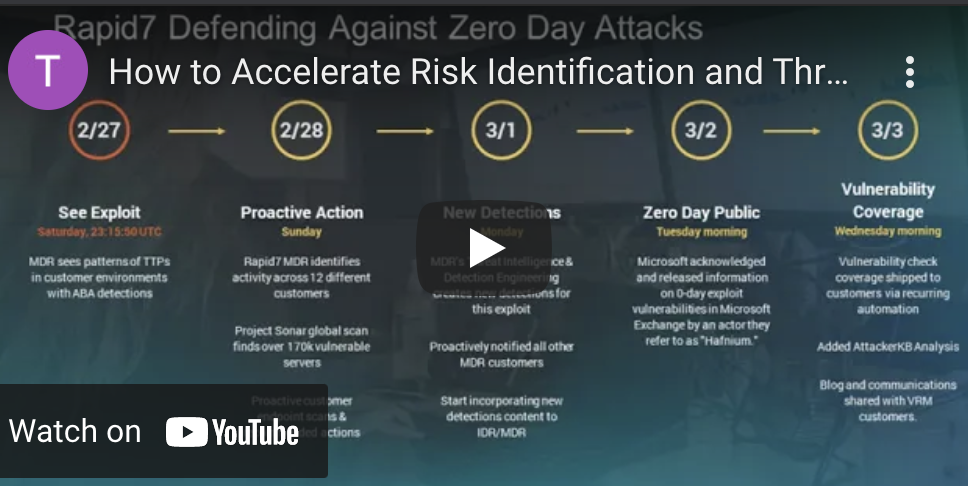
Discover how security teams battle the complexities of the industry with the Rapid7 InsightPlatform. The InsightPlatform is a holistic, cloud-based platform that can help accelerate threat detection and remediation with expansive visibility and risk coverage to minimize the attack surface. Watch this 10 minute talk to learn how the InsightPlatform leverages analytics, context and automation to detect and extinguish threats.
Read more ›Post Tagged with: "gf_row"

The Rise of Cloud-Based Security Analytics and Operations Technologies
How can CISOs address these issues and develop effective security analytics and operations processes? In order to get more insight into these trends, ESG surveyed 372 IT and cybersecurity professionals at organizations in North America (U.S. and Canada) responsible for evaluating, purchasing, and managing threat detection/response products, processes, and services. This eBook will cover how external changes and internal inefficiencies […]
Read more ›
Dark Reading Malware Threat Landscape Report
Cybercriminals have ramped up attacks against organizations and are compromising them in greater numbers than a year ago. Phishing and viruses remain the most commonly detected attacks on enterprise networks, but ransomware and business email compromise (BEC) attacks could become the biggest threats over the next two years. Explore the Malware Threat Landscape report to explore survey results revealing concerns […]
Read more ›
A SANS 2021 Report: Making Visibility Definable and Measurable
Visibility does not lend itself to a precise definition—the meaning will differ depending on who is looking. Yet organizations need to establish a visibility strategy that complements their security profile in order to assess where they should direct resources to improve for the future. To achieve this, organizations need to take an interdisciplinary approach, as SANS did in this report. […]
Read more ›
Better Together: 10 Ways to Turbocharge Active Directory With One Identity Active Roles
Maintaining Active Directory (AD) in a clean, organized and secure state is a challenge, particularly for user accounts. Learn 10 steps you can take to clean up your Microsoft AD/AAD user account data. This process is key to efficiency, security and compliance. We will take you through each step; demonstrate why it’s important and what it will enable your team […]
Read more ›
Choose the Best Graph Database Using This Buyer’s Guide
Selecting a graph database is an important decision that can shape the success of your organization. This guide is intended to assist your buying decision with side-by-side comparisons of graph databases from Amazon, DataStax, Neo4j and TigerGraph.
Read more ›
2021 Global Security Insights Report
Accelerated digital transformation has caused security teams to face a surge in cyberattacks targeting the anywhere workforce. Globally businesses are battling a sustained threat environment where attacks continue to grow in sophistication and complexity, making breaches an all but inevitable consequence. Our fourth edition of the Global Security Insights Report surveyed 3,542 CIOs, CTOs and CISOs in 14 countries to […]
Read more ›
U.S. Security Insights Report
The disruption of the pandemic along with the anywhere workforce resulted in a surge of sophisticated cyberattacks and material breaches. 63% of U.S. cybersecurity professionals said attacks increased due to employees working remotely. Security teams now face the challenge of securing the anywhere workforce. The new workforce has created blind spots and a lack of visibility, highlighting the vulnerabilities in […]
Read more ›