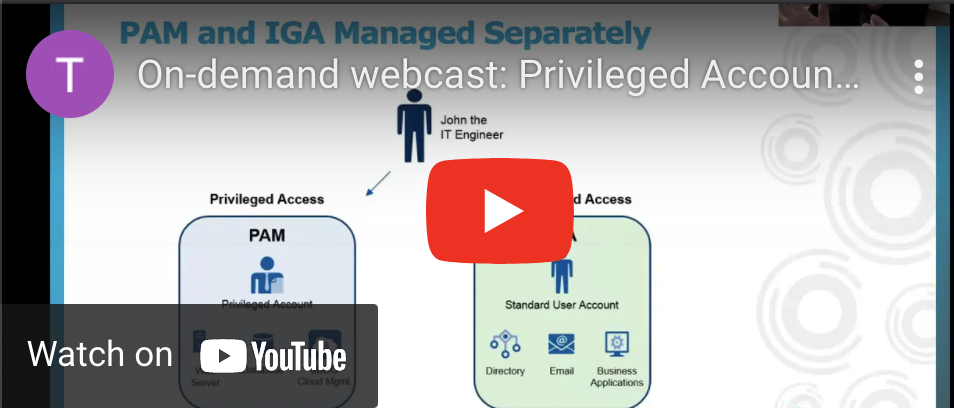
The term ‘privileged access’ is a hot topic lately. It refers to connecting to and managing your critical accounts, which enable your organization to run smoothly. Protecting these accounts should be the first priority when it comes to cybersecurity. With everything you and your team have going on – including making your digital transformation – and the constant threat of […]
Read more ›Post Tagged with: "gf_row"
On-Demand Webcast: Extending Identity Governance to the Cloud
Whether it’s your digital transformation or the pandemic – or a combination of both – that has your organization becoming more reliant the cloud, you now understand the need to extend the identity governance processes you run with on-premises systems to your cloud/SaaS resources.Protecting your data regardless of where it flows to and from, and where it is stored, is […]
Read more ›
Directory Management Chaos in the Cloud
The cloud has significantly evolved over the last decade from a technology you should be using, to the established solution set for everything from commodity virtual resources and flexible infrastructure, to entire platforms and applications. Because of this, organizations like yours have shifted operational models to take advantage of any and all that the cloud has to offer. Strategies include […]
Read more ›
Peer Paper Review: 10 Best Practices for Managing and Securing Microsoft Active Directory in an Evolving IT World
Identity and Access Management (IAM) programs reliably center around Microsoft Active Directory (AD) and Azure AD (AAD) as their foundation. However, as IAM environments move to the cloud, modernize and extend toward governance, IT managers are pained with security and efficiency gaps in native AD, and as such they seek solutions to augment the capabilities of AD which often fall […]
Read more ›
PerimeterX is Named a Leader in Bot Management by Forrester
PerimeterX was named a leader in The Forrester New Wave™: Bot Management, Q1 2020. According to the report, PerimeterX “leads the pack with robust machine learning and attack response capabilities” and includes a customer quote stating that PerimeterX Bot Defender “was extremely easy to deploy in production and maintain.” PerimeterX Bot Defender is the behavior-based bot management solution for any […]
Read more ›
CISOs Guide to ATO Against the Digital Storefront
For any major online storefront, account takeover (ATO) attacks are a growing threat. ATO fraud for ecommerce merchants rose 282% between Q2 2019 to Q2 2020, according to recent research. ATO attempts should be on the radar of CISOs as a top business and compliance risk for 2021. This whitepaper provides a guide for CISOs and other security leaders to […]
Read more ›
Cyberthreat Infographic 2021
CyberEdge Group’s eighth annual Cyberthreat Defense Report reveals how IT security professionals perceive the security posture of their organizations and the challenges they face establishing effective cyberthreat defenses.
Read more ›
Digital Transformation and the Shadow Code Risk
Web application developers often rely on open source JavaScript libraries and third-party scripts in order to innovate faster and keep pace with evolving business needs. However the lack of visibility and control of these third party scripts and libraries introduces vulnerabilities that can negatively impact the security and privacy posture of your website leading to fines and brand damage. Read […]
Read more ›