The VMware Service-Defined Firewall intrinsically embeds self-learning, adaptive micro-segmentation and app control into the infrastructure, eliminating the need to bolt on additional products, deploy agents, or engage in complex configuration processes. VMware is committed to helping customers quantify the value of their investment and continuously validate that the Service-Defined Firewall is effectively deployed and configured in dynamic IT environments. VMware […]
Read more ›Post Tagged with: "gf_row"

Evolving Micro-Segmentation for Preventative Security
Network security has changed significantly during the past several decades, and it’s time to rethink the way we’re approaching it today. To start, we need to embrace the idea of software-defined micro-segmentation. This SANS whitepaper addresses a few key changes we need to address: • Looking at our entire environment as potentially untrusted or compromised, versus thinking in terms of […]
Read more ›
Cloud Migrations with VMware CloudTM on AWS Solution Brief
Organizations migrate to the cloud to support business growth, drive digital transformations, improve development cycles and to optimize costs. During this transition, several migration and post-migration challenges emerge that increase time, risk and costs associated with successful completion of such projects. Read on to see how VMware Cloud on AWS solves these migration challenges by delivering a hybrid cloud service […]
Read more ›
Global MIT Report: After Deployment Storms, Skies Turn Sunny for Multi-Cloud Environments
What does digital transformation mean and what does it look like? How does a company change itself to become more competitive? This new worldwide survey produced by MIT Tech Review Custom and sponsored by VMware, provides a detailed snapshot of digital transformation in action. The study identified large companies that had adopted a multi-cloud infrastructure, and asked 1,350 C-suite executives […]
Read more ›
Why HR Spreadsheets Stink and What to Do About Them
Why using spreadsheets to manage HR data stinks, what it’s costing you, and what to do about it. You don’t have to be a slave to your spreadsheets. There are better options that will actually save you time and money.
Read more ›
13 Tips for Small Businesses to Recruit and Retain Talent
Great talent is at the heart of every great company, which is why HR is always thinking about finding, bringing on and keeping great people. That’s why BambooHR CEO Ben Peterson and Cornerstone OnDemand’s VP of Small Business Operations Michael Carden came together to share 13 proven tips for small business to recruit and retain great talent.
Read more ›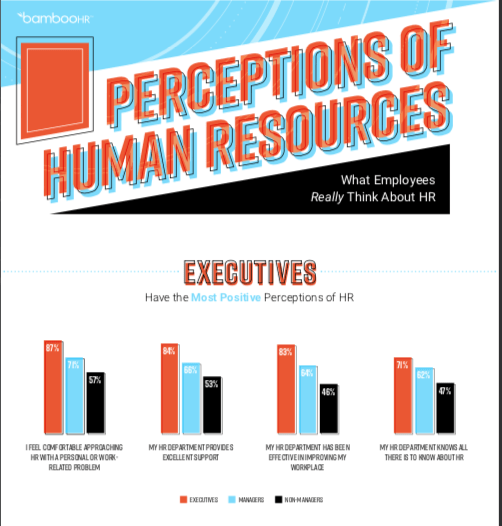
Perceptions of Human Resources
Admit it: You care what people think about you. It’s human nature. Whether it’s a neighbor, a new group of friends, or coworkers, people spend a lot of time curating their image and wondering how others perceive it. While we haven’t figured out what your neighbor thinks about living next to you, we can tell you what people at your […]
Read more ›
Calculating HR: The Real Value of HR Software
From reducing turnover to boosting employee experience, HR has a lot to offer. But if all of HR’s time is eaten up by day-to-day tasks like answering benefits questions or tracking time off, they’ll never be able to take on more strategic initiatives. HR software can automate many of the processes that consume valuable time in your organization. Take a […]
Read more ›


