PlanGrid partnered with FMI Corporation to survey construction leaders about how teams spend time and leverage technology investments. The results indicate that time spent on non-optimal activities such as fixing mistakes, looking for project data and managing conflict resolution accounts for $177.5 billion in labor costs per year in the U.S. alone. The study found that rework caused by miscommunication […]
Read more ›Post Tagged with: "gf_row"

Connected, Anywhere. 8 Field Focused Challenges in Heavy Civil Construction And How to Overcome Them
Weak technology in the field has historically limited improving how Heavy Civil and Infrastructure projects are approached. When field teams are unable to communicate and receive real-time feedback from engineers and designers, entire projects suffer. The ability to curtail costs and complete work within budget is key to managing the world’s growing infrastructure needs. In our e-book, we discuss the […]
Read more ›
IDG Countering Escalating Cyberthreats with a New Security Architecture
IDG survey confirms: CEOs consider cybersecurity a top priority. Get “Countering Escalating Cyberthreats” and improve your threat visibility across the entire network. As CEOs struggle with the risks of a digital business, it is time to adopt a more holistic approach to security. You can distribute traffic to the right tool at the right time, eliminate network weaknesses and keep […]
Read more ›
ESG Research Report: Network Security Trends
Read “Understanding the State of Network Security Today” to learn why ESG recommends consolidating security tools through a structured, platform-based approach. Data, analytics and reports from multiple tools can be aggregated and consumed in one control panel, reducing network vulnerabilities. Learn more about challenges, changes and best practices for today’s network security operations and tools. Read now.
Read more ›
Harnessing the Power of Metadata
Read the Gigamon paper, “Harnessing the Power of Metadata for Security,” to see why metadata is the new security super power. Metadata is data about data. It is a summary or high-level view of data. Providing security tools with a summary of the packet data traversing networks, metadata becomes a powerful weapon for enterprises looking to separate signals from noise, […]
Read more ›
IDG CSO: Security Should be an Enabler
Perimeter-based solutions for network security do not work, leading to tool sprawl and performance issues. Read CSO Magazine’s interview with Gigamon CISO, Simon Gibson, to learn why a new, more intelligent approach is needed to build resilience into technology operations. “Security Should Be an Enabler” talks about an architectural approach that distributes only relevant data to appropriate tools, enabling an […]
Read more ›
Rethink Network Security Deployment
Download the Gigamon white paper, “Addressing the Threat Within: Rethinking Network Security Deployment”, to learn how evolving cybersecurity threat conditions are changing the trust model for security. See how a structured and architectural approach to network security gives security solutions better access to network traffic while enabling them to scale cost effectively. Learn how a security delivery platform can be […]
Read more ›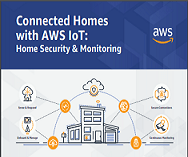
Infographic: Connected Homes with AWS IoT: Home Security & Monitoring
Home Security & Monitoring in the Connected Home with AWS IoT With 940M smart home devices expected to be shipped worldwide by 2022, the connected home market segment is booming. Download this infographic to learn how AWS IoT’s suite of software and services helps protect data, devices, and consumers, bringing home security & monitoring to the cutting edge.
Read more ›


