Continuous monitoring (CM) can result in continuous improvement that reduces attack surfaces and improves security postures according to this 2016 survey of 292 individuals actively involved in vulnerability assessment and remediation. 63% of respondents said CM was improving their security posture.
Read more ›Post Tagged with: "gf_row"

Cloud Based It Asset
Complete, unobstructed visibility of your IT environment is the foundation for effective cybersecurity. Without a full, detailed inventory of all your IT assets, your InfoSec team won’t be able to properly protect your organization because the things that pose the highest risk are the ones that you don’t know are there. For a long time, this basic requirement was fairly […]
Read more ›
Excel Security Assessments Without Excel Spreadsheets
Are your vendors and other business partners putting your organization at risk? How compliant with information security standards, government regulations and internal policies are the third parties your organization does business with? Download this white paper to learn more about excel security assessments without excel spreadsheets.
Read more ›
Prioritizing Vulnerability Remediation Age Threat Disclosure Overload
One of the biggest challenges faced by information security teams today is how to effectively prioritize their vulnerability remediation work. Why? New vulnerabilities are disclosed every day, amounting to thousands per year. Burdened with this overload of vulnerability disclosures, infosec teams often get overwhelmed by the task at hand and throw up their hands in frustration. After all, no IT […]
Read more ›
Top 5 Requirements Prioritizing Vulnerability Remediation
IT departments are overwhelmed by the abundance of vulnerabilities that continue to grow at a rapid pace every day. They struggle to identify the most critical threats they must address right away at any given point to protect their organizations from a compromise. Attempting to eradicate 100 percent of vulnerabilities sequentially, by treating them all as equally important, is impractical, […]
Read more ›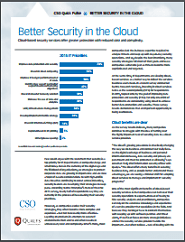
Better Security in The Cloud
Few would argue with the statement that cloud-based security is a top priority for IT departments at companies large and small today. Data is the currency of the digital age and the lifeblood of organisations, so strategies to protect corporate data are growing in importance and are now a topic of C-suite consideration. So with high-profile data breaches continuing to […]
Read more ›
20 Critical Security Controls
It’s not easy being today’s CISO or CIO. With the advent of cloud computing, Shadow IT, and mobility, the risk surface area for enterprises has increased dramatically, while IT budgets have shrunk and skilled cyber security talent is virtually impossible to find. Thankfully, the CIS Top 20 Critical Controls provides a pragmatic approach, offering prioritized guidance on the important steps […]
Read more ›
Best Practices for Selecting a Web Application Scanning (WAS) Solution v3
With attackers getting more sophisticated every day, manual methods of locating and testing web-based apps are no longer enough. The right Web Application Scanning (WAS) solution can help you systematically: discover web apps running in your network, determine whether or not they are vulnerable to attack, understand how to fix them, and protect your business while fixes are being implemented. […]
Read more ›


